
Data sovereignty is no longer a legal footnote. It's a balance sheet issue.
For CFOs, the question is no longer "Are we compliant?" but "Can we prove it, in real time, under scrutiny, without burning a quarter’s worth of resources doing so?"
When data crosses borders without control, the financial impact is swift and silent: fines, audit delays, legal overages, and margin leakage.
And yet, many organisations still treat data sovereignty like a tick-box exercise. A policy statement. A slide in a compliance deck.
That’s a costly illusion.
At Gatekeeper, we built our platform from day one to give finance and compliance leaders the controls they need to manage risk, cost, and complexity in a world where data governance is inseparable from business performance.
The impact of jurisdictional data exposure lands directly on the CFO’s desk:
This isn’t hypothetical. Audits today don’t just ask where your contracts are stored. They ask where they were processed, analysed, summarised, or transformed by AI. If you can’t evidence that trail with confidence, the cost shows up fast.
Gatekeeper was built to give CFOs certainty. By unifying contract, third-party, and spend data in a single platform - governed by regional hosting and jurisdiction-aware AI - we replace guesswork with control, and surprises with predictability.
In principle, data sovereignty is simple: data should remain subject to the laws of the country where it originates. In practice, it’s anything but.
Most SaaS vendors operate on a lowest-common-denominator model: one global instance, one data centre, and a one-size-fits-none approach to compliance. But for regulated and compliance-driven businesses, that model is obsolete. When contracts, vendor files, and risk data leave the region, so does your control, your audit trail, and your regulatory posture.
Gatekeeper takes a different path - because we serve companies where sovereignty isn’t a preference, it’s a mandate.
Cloud computing dissolved borders. And AI is now dissolving control.
Behind every SaaS platform is a complex web of hosting providers, subprocessors, and increasingly, generative AI models that may process your data without your awareness or consent. Even if your contract or vendor data is hosted in-region, it can still be routed to large language models hosted offshore for processing.
That means sensitive documents could be copied, cached, and analysed in jurisdictions where you have no legal standing.
Most customers assume their data stays where it was stored. But with the wrong AI architecture, "in-region" becomes a myth. Compliance claims may hold up for storage - but fall apart under scrutiny when it comes to processing.
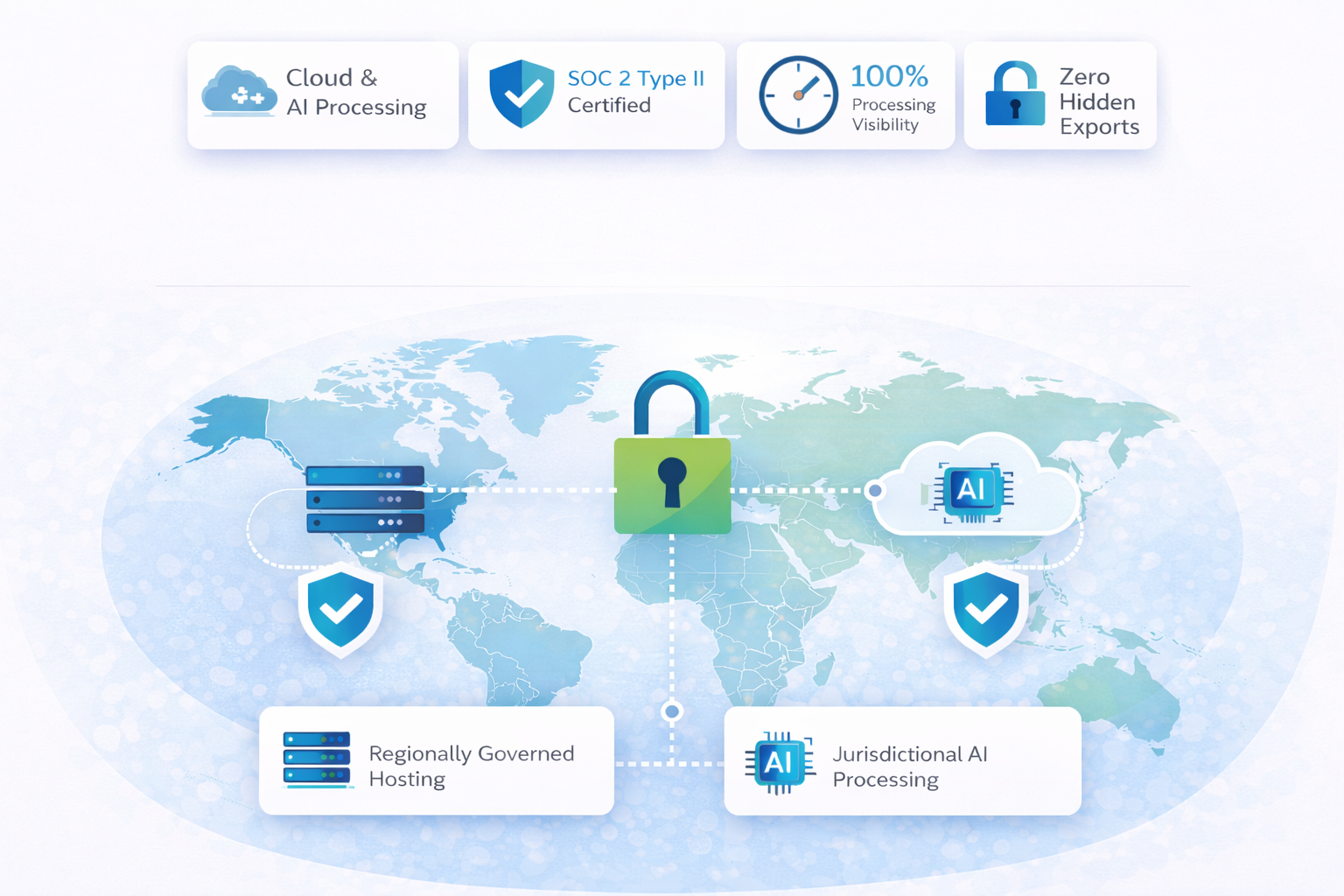
At Gatekeeper, we built our platform with this blind spot front of mind. Every data interaction is governed, every processing path is visible, and jurisdictional boundaries are enforced by design. There are no hidden exports or silent transfers to offshore environments.
And with SOC 2 Type II certification, via Insight Assurance, covering our operations in the US, UK, Canada, and Jersey, we don’t just claim compliance - we evidence it.

Data sovereignty has shifted from a compliance concern to an operational reality. Data now moves across borders via cloud infrastructure, analytics layers, subprocessors, and AI - often without visibility.
Many platforms point to "regional hosting" as proof of compliance. But sovereignty isn’t about where data is stored. It’s about how it’s accessed, processed, and evidenced over time.
Without enforceable controls and audit trails, sovereignty becomes an assumption. And assumptions don’t survive audits.
We’ve seen it repeatedly: organisations believe their data is protected because it's stored locally. But in reality, data flows through undocumented subprocessors, foreign-hosted AI services, and jurisdictionally ambiguous APIs.
The result is a widening gap between policy and proof.
When regulators ask how data was handled end-to-end, many organisations simply can’t answer. That’s not just a compliance issue. It’s a financial liability.
Gatekeeper was designed to serve compliance-driven organisations that need defensible, real-time governance over contract, third-party, and spend data.
We enable sovereignty through:
These aren’t add-ons. They’re embedded by design.
Gatekeeper protects customer data through a layered control architecture:
These protections are built to reduce reliance on manual oversight and eliminate hidden exposure.
Today, data sovereignty requires more than vendor assurances or policy statements. It requires verifiable controls, documented processes, and audit-grade evidence.
Gatekeeper enables customers to move from assumption to certainty by embedding governance directly into how they manage contracts, vendors, and spend.
Because for modern CFOs, sovereignty isn’t about where the data sits. It’s about whether you can prove it, defend it, and control it - at any moment.
And that’s what we built Gatekeeper to deliver.
See how Gatekeeper delivers real-time visibility, jurisdiction-aware processing, and audit-ready evidence.
.png)
.png)
.png)
-4.png)
Before Gatekeeper, our contracts
Anastasiia Sergeeva, Legal Operations Manager, BlaBlaCar
were everywhere and nowhere.
Gatekeeper is that friendly tap on the shoulder,
Donna Roccoforte, Paralegal, Hakkasan Group
to remind me what needs our attention.
Great System. Vetted over 25 other systems
Randall S. Wood, Associate Corporate Counsel, Cricut
and Gatekeeper rose to the top.
Thank you for requesting your demo.
Next Step - Book a Call
Please book a convenient time for a quick call to discuss your requirements.