

Australian Prudential Standard CPS 234 Information Security was created to enhance resilience around security incidents. It focuses mainly on cyber attacks for APRA-regulated entities that need to maintain information security capabilities to protect their organisation and customers.
You’ll want to consider this alongside your APRA CPS 230 requirements.
For vendor-facing teams, you likely provide your vendors with sensitive information or that they control swathes of information in the services performed.
The likelihood of cyber attacks in a supply chain is high.
According to a Security Scorecard and the Cyentia Institute report, 98% of companies have had one of their vendors breached in the last two years. The National Cyber Security Centre (NCSC) also emphasises the importance of understanding supply chains to mitigate cyber risk.
In this article, I’ll explore how we can utilise a Vendor and Contract Lifecycle Management (VCLM) platform and methodology to ensure your vendors and the wider supply chain are CPS 234 compliant.
A good starting point is to look at your existing vendor controls and governance capabilities. CPS 234 is a collaborative requirement.
You’ll likely need your teams aligned on the strategy across:
One way to enhance your approach is to create a committee with stakeholders from each team to oversee CPS 234 requirements.
I regularly attended and was part of a risk committee during my time in FinTech. We were able to cover just about every regulatory, legislative, and “other” scenario that the organisation may face and build out ways of working across multiple teams to manage it.
Building a 'Responsible, Accountable, Consulted, and Informed' (RACI) chart for CPS 234 makes sense to ensure everyone is clear on their responsibilities and accountabilities, and this seems to go hand-in-hand with Section 14 requirements, which state:
“An APRA-regulated entity must clearly define the information security-related roles and responsibilities of the Board, senior management, governing bodies, and individuals with responsibility for decision-making, approval, oversight, operations and other information security functions”.
Governing bodies also allude to committees such as those I’ve mentioned, so having a clear committee policy, with chairs, scribes, and all that good stuff, is necessary.
Once you’ve implemented this, you’ll have a forum to discuss and collaborate. More importantly, it forces all the issues into a single melting pot.
CPS 234 has several requirements that vendor-facing teams will need to consider. I’ve highlighted the extent of the requirements in this summary of the original text. Entities must:
As you can see, there are many "vendor-facing” requirements here that we need to manage.
I’ll walk you through using Gatekeeper’s VCLM platform to become APRA CPS 234 compliant.
I’m going to focus on several areas here:
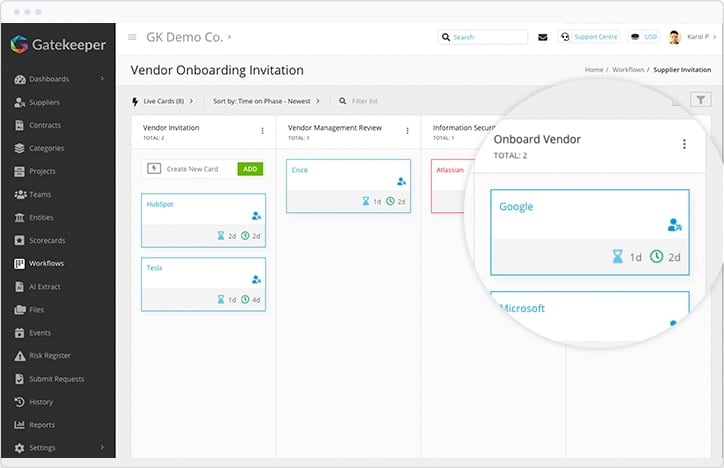
Using a vendor onboarding best practice workflow, you can get up and running with CPS 234 compliance speedily.
Within the Gatekeeper vendor onboarding workflow, you can create a set of CPS 234 due diligence questions. Likely, you’ll already have some relevant questions. These questions will focus on:
This data can be stored, accessed, and viewed in reporting to give you complete visibility and control over your CPS 234 compliance requirements.
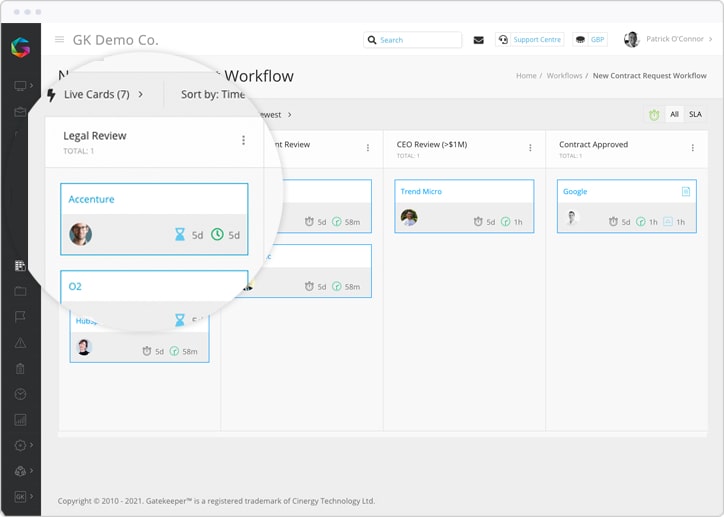
The best way to ensure contract compliance is through a digital workflow. By utilising Gatekeeper’s contract review best practice workflow, you can manage:
Ensure you have clauses in your contracts around the following:
You can use the contract review workflow to capture this information and ensure it’s all in place before the contract signature. That way, every vendor contract achieves 100% CPS 234 compliance.
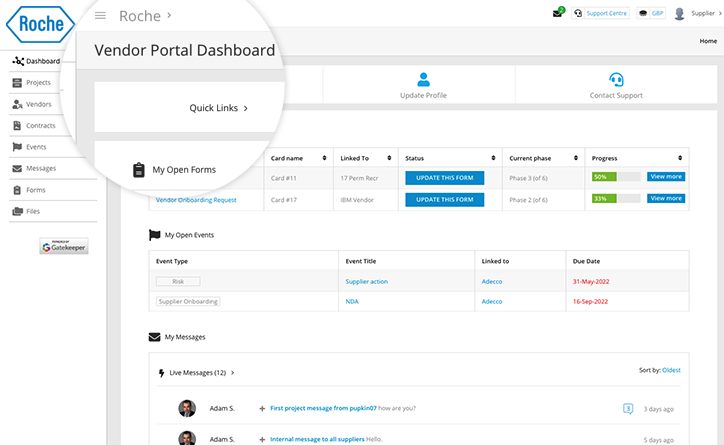
An under-appreciated solution to vendor compliance requirements is having a vendor portal so that your vendors can communicate and collaborate with you securely.
You’ll be able to create a vendor portal account for your vendors, invite relevant vendor users and collaborate with them.
You’ll have all your vendor personnel responsible for incident management in one place.
Your vendors can update you on matters via the portal, update their information, and provide up-to-date documents such as their Information Security Management Strategy documentation as needed upon expiration of the current version.
CPS 234 will require vendor management to play its part in assisting the wider business. I don’t see this as something vendor-facing teams will necessarily lead on, but you will ensure your organisation complies.
Utilising a VCLM approach might be the perfect way to ensure that your vendors, their contracts, and their risk profiles are suitable for your compliance requirements.
Ready to improve your contract & vendor management?
.png)
.png)
.png)
-4.png)
Before Gatekeeper, our contracts
Anastasiia Sergeeva, Legal Operations Manager, BlaBlaCar
were everywhere and nowhere.
Gatekeeper is that friendly tap on the shoulder,
Donna Roccoforte, Paralegal, Hakkasan Group
to remind me what needs our attention.
Great System. Vetted over 25 other systems
Randall S. Wood, Associate Corporate Counsel, Cricut
and Gatekeeper rose to the top.
Thank you for requesting your demo.
Next Step - Book a Call
Please book a convenient time for a quick call to discuss your requirements.