

The Digital Operational Resilience Act, known as DORA, will soon be in force and it will have a dramatic impact on your vendor contracts.
We recently created a DORA summary and in this article, I’m going to explain:
The EU expects public authorities to develop standard clauses to address DORA regulatory needs around mandatory clauses.
It suggests financial services companies and ICT third-party vendors use such language when available. However, I’d suggest you get ahead and work on standard wording that you can add to your contracting clause bank ahead of time.
Every ICT Services contract you have must:
You must also report annually on “the number of new arrangements on the use of ICT services, the categories of ICT third-party service providers, the type of contractual arrangements and the ICT services and functions which are being provided. (Article 23 (3)).
Article 28 (1) (a) states:
“financial entities that have in place contractual arrangements for the use of ICT services to run their business operations shall, at all times, remain fully responsible for compliance with, and the discharge of, all obligations under this Regulation and applicable financial services law”.
You’ll need to ensure that your vendors are flowing contract clauses down through their supply chains. You should also deploy effective contract management otherwise you may fall foul of being “fully responsible”.
Before signing any vendor contract that falls within the remit of DORA, you’ll need to carry out the following six activities.
DORA is focused on those contract arrangements that truly matter and it terms them critical or important. Critical vendor contracts incur a higher level of compliance requirements.
By way of an analogy, we would not care about a subscription to Canva for the marketing team as this does not constitute a “critical” service. However, for a financial services company, using a software provider that enables you to identify hidden proxies that might be used to commit fraud is likely to constitute a “critical” or “important” vendor and contract arrangement.
You’ll need to review all your vendors to understand their importance to your organisation. Then, you should apply appropriate categorisation and vendor segmentation.
The requirement to "assess if supervisory conditions for contracting are met" focuses on ensuring that financial entities assess and comply with specific conditions or requirements when contracting ICT services.
These supervisory conditions can include various aspects such as security, data protection, and operational resilience.
The goal is to ensure that any third-party service providers or ICT services these financial entities use meet strict standards that align with the overall objectives of DORA to maintain operational resilience.
As you’d expect, there is a strict requirement for risk management in Article 28.4.(c). It states:
“Identify and assess all relevant risks in relation to the contractual arrangement, including the possibility that such contractual arrangement may contribute to reinforcing ICT concentration risk as referred to in Article 29”.
Let’s break this down.
a) Relevant Risks Assessment
Financial entities must conduct comprehensive assessments of all risks associated with their contractual arrangements with ICT third-party service providers.
This isn't just about the immediate risks of service disruption or data breaches.
It extends to broader considerations such as the impact on the entity's overall operational resilience.
b) ICT Concentration Risk
A specific focus is placed on assessing the potential for ICT concentration risk, referring to the scenario where too many entities in the financial sector rely on a limited number of ICT service providers.
This could lead to systemic vulnerabilities if one of these providers fails or experiences significant issues.
If your business has concentrated risk, you might need to change how you work.
The ideal scenario is that you have a digital workflow in place for all of your contract reviews. You can then have a dedicated Risk Identification phase where you spend time assessing potential issues. Commit them to a vendor risk register that enables you to manage or accept the risk as is.
Before entering into any contractual agreement, financial entities are expected to vet prospective ICT third-party service providers.
This due diligence process involves evaluating the provider's:
This is vendor management best practice and we’d highly recommend you do this for every vendor you onboard.
Vendor onboarding is simple when you have a VCLM platform.
Once a request is raised via the Employee Portal to onboard a new vendor, you can complete all your checks using pre-built forms and live risk data utilising the Market IQ suite.
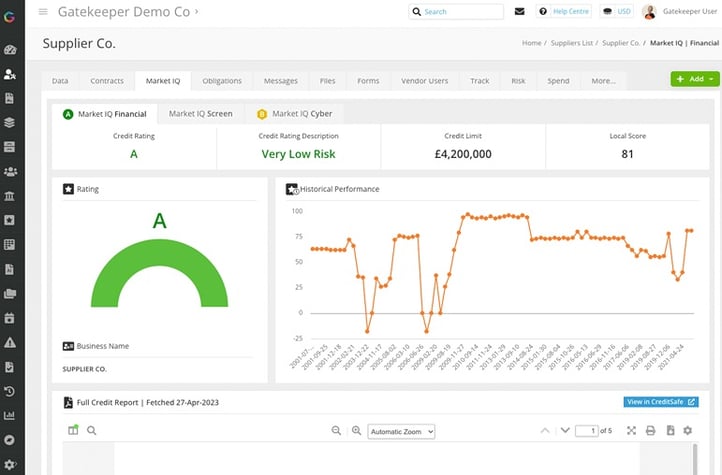 Gatekeeper's method for managing vendor credit and cyber risks 24/7/365
Gatekeeper's method for managing vendor credit and cyber risks 24/7/365
The vendor selection process should be rigorous and transparent, ensuring that the chosen ICT third-party service provider aligns with the financial entity's needs and regulatory obligations.
This might mean you adopt a more agile procurement process to assess and negotiate with multiple vendors in this space.
Financial entities must proactively identify and assess potential conflicts of interest with ICT third-party service providers.
Conflicts of interest could compromise the impartiality or integrity of the services provided and potentially pose risks to the entity's operational resilience."
After identifying potential conflicts of interest, financial entities must take appropriate steps to manage, mitigate, or eliminate them.
This might involve:
With the Market IQ Suite from Gatekeeper, you can identify potential conflicts of interest in ownership by using our integration with Security Scorecard.
Article 28.5 states:
“Financial entities may only enter into contractual arrangements with ICT third-party service providers that comply with appropriate information security standards. When those contractual arrangements concern critical or important functions, financial entities shall, prior to concluding the arrangements, take due consideration of the use, by ICT third-party service providers, of the most up-to-date and highest quality information security standards”.
This requirement safeguards financial entities, ensuring their data and ICT systems are protected against cyber threats and vulnerabilities through established security practices.
An assessment might involve reviewing certifications, audit reports, or other documentation that evidences compliance.
You can build these checks into the vendor onboarding process. From there, you can maintain compliance effortlessly by building a file expiry workflow to automate the capture of updated certificates, reports and documents. These can be reviewed with the wider team.
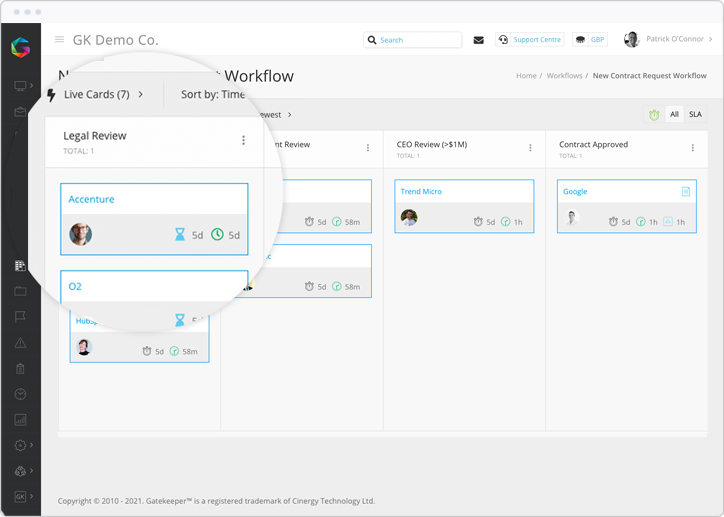
For many people still operating manually, this will be a monumental challenge. However, if you are utilising a VCLM approach this should be easy to deploy.
Here’s a checklist of what you need when it comes to DORA-compliant contracts:
When it comes to provisions that require assistance, collaboration, and involvement in your operational resilience training, it’s unlikely you’ll have these in place with existing vendors.
I want to focus on two of these provisions that might require more work than the others: termination and exit strategies.
Article 28.7 states:
Financial entities shall ensure that contractual arrangements on the use of ICT services may be terminated in any of the following circumstances:
(a) significant breach by the ICT third-party service provider of applicable laws, regulations or contractual terms;
(b) circumstances identified throughout the monitoring of ICT third-party risk that are deemed capable of altering the performance of the functions provided through the contractual arrangement, including material changes that affect the arrangement or the situation of the ICT third-party service provider;
(c) ICT third-party service provider’s evidenced weaknesses pertaining to its overall ICT risk management and in particular in the way it ensures the availability, authenticity, integrity and, confidentiality, of data, whether personal or otherwise sensitive data, or non-personal data;
(d) where the competent authority can no longer effectively supervise the financial entity as a result of the conditions of, or circumstances related to, the respective contractual arrangement.
Points (b) and (c) will need additional work as it is unlikely that you will have these in your current contracts.
Any existing agreement that isn't compliant with DORA must be moved into a contract amendment workflow so you can incorporate additional terms in a structured and auditable format. Learn more about this in our webinar below.
DORA mandates financial entities to develop robust exit strategies for ICT services that support critical or important functions, emphasising operational resilience and regulatory compliance.
Here's a summary of the key requirements:
For many in the Financial Services, you’ll already be under the EBA remit and your outsourcing requirement will be in place.
However, there will be a large number of organisations that fall under the DORA remit that don’t have that same level of maturity. They will need to get ahead and be in a good place by the end of Q3 2024.
The best way to tackle this is through VCLM as it takes care of the three critical components of DORA:
If you’re tired of using spreadsheets, outdated emails, and working in chaos, book a call to speak with one of our VCLM experts to help you get DORA-compliant.
Ready to improve your contract & vendor management?
.png)
.png)
.png)
-4.png)
Before Gatekeeper, our contracts
Anastasiia Sergeeva, Legal Operations Manager, BlaBlaCar
were everywhere and nowhere.
Gatekeeper is that friendly tap on the shoulder,
Donna Roccoforte, Paralegal, Hakkasan Group
to remind me what needs our attention.
Great System. Vetted over 25 other systems
Randall S. Wood, Associate Corporate Counsel, Cricut
and Gatekeeper rose to the top.
Thank you for requesting your demo.
Next Step - Book a Call
Please book a convenient time for a quick call to discuss your requirements.