

Understanding your full vendor portfolio, including costs, distribution, key milestones and performance can be a challenge and can be a blocker to implementing a coherent vendor strategy.
As custodians of your business’s networks and information, your primary concern is keeping it safe and secure.
Knowing the location of your data is vital to meet data sovereignty requirements.

Tracking costs across a shifting vendor set and maintaining control over new vendor approval requires robust processes and universal adoption.
Gatekeeper stores interactions with your suppliers automatically. Centralise contracts, files, supplier contacts and track supplier performance.
Collaborate with any internal or external stakeholders within a single secure platform.
.png)
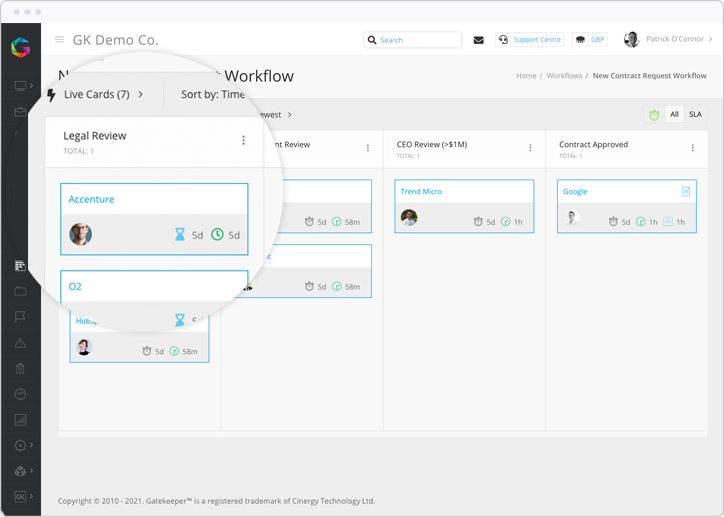
Digitise and visualise all company processes with our industry unique Kanban Workflow Engine.
Automate your processes to run 24/7 and set SLAs to keep momentum and meet compliance requirements.
Role Based Access Control (RBAC)
Manage user access roles to a granular level with a detailed breakdown of all user ownerships and access.
SCIM Provisioning
System for Cross-domain Identity Management (SCIM) support to provision users and set Role Based Access Control (RBAC) remotely from our customers’ SSO solution. *Coming soon.*
Two-factor authentication (2FA)
Two-factor authentication support within our core application and partner SSO solutions.
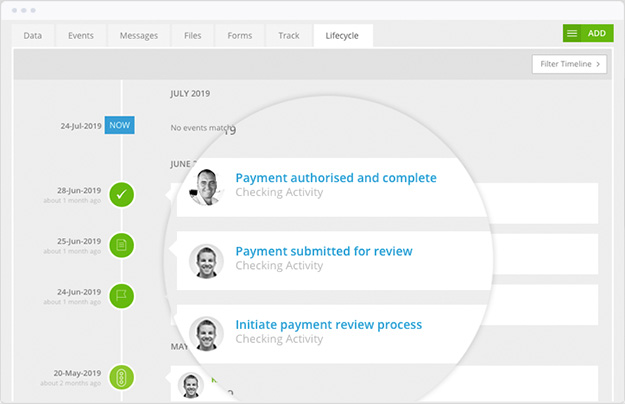
Financial-grade user and data audit logs for all activity supported by a range of reports.
Every action relating to every contract and vendor is recorded in an easily-reviewable, fully defensible timeline.
Capture risks by supplier, type & category and assign ownership and due dates to set mitigation expectations.
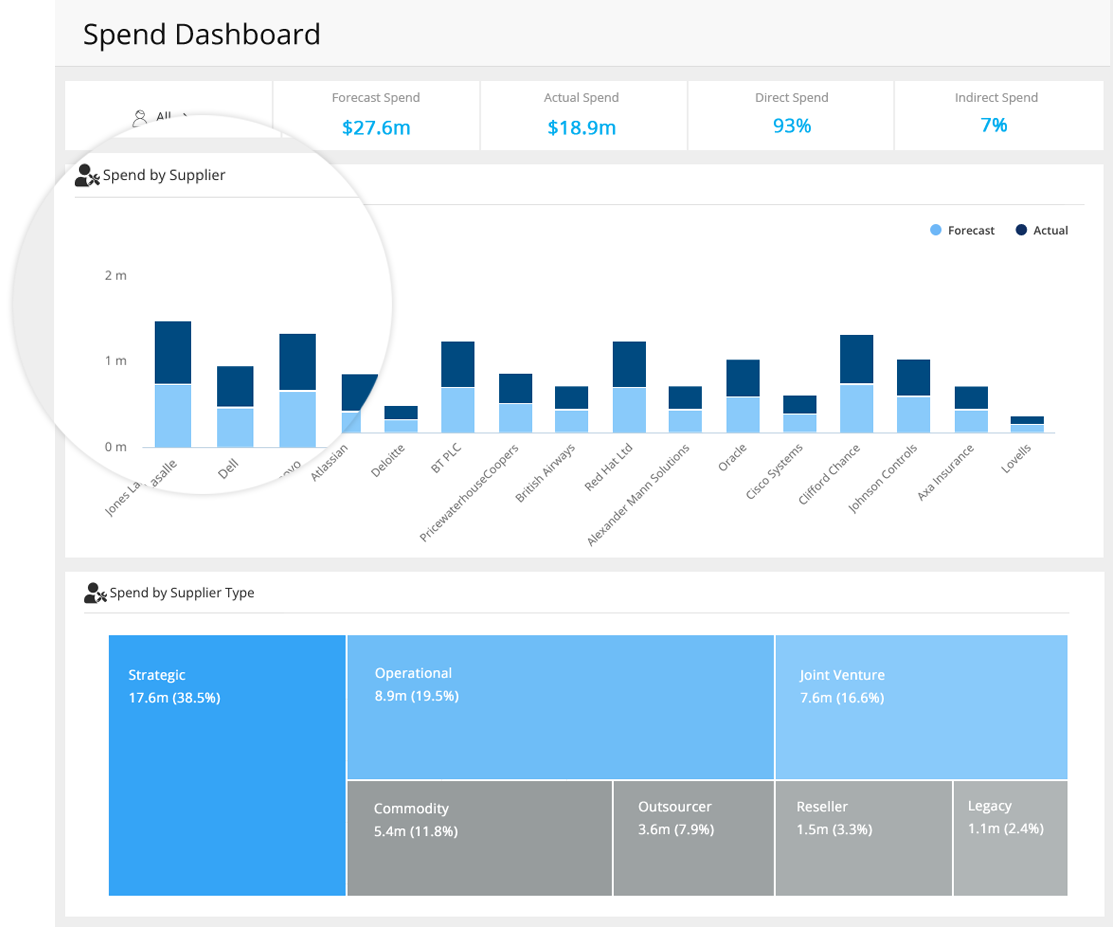
Use our Spend Dashboard to track actual vs expected / direct vs indirect and drill down into detailed reports to identify maverick or excess spend.
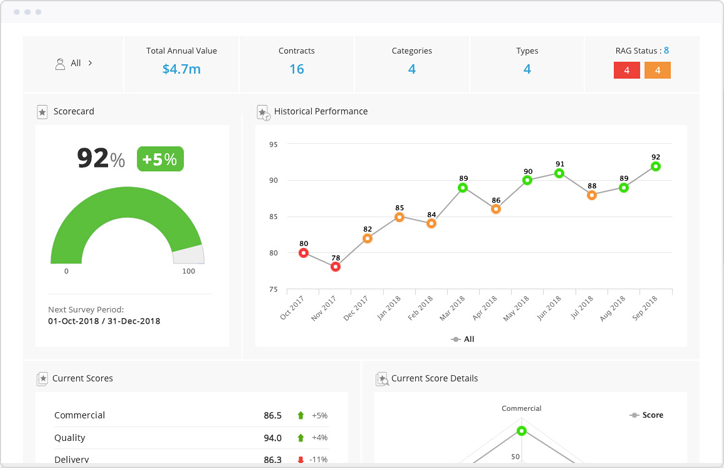
Measure, collect and analyse vendor performance using our Balanced Scorecards module.
Gather stakeholder feedback and plot results on a tailored grid to understand your vendor portfolio’s strengths and weaknesses.






.png)
.png)
.png)
-4.png)
Before Gatekeeper, our contracts
Anastasiia Sergeeva, Legal Operations Manager, BlaBlaCar
were everywhere and nowhere.
Gatekeeper is that friendly tap on the shoulder,
Donna Roccoforte, Paralegal, Hakkasan Group
to remind me what needs our attention.
Great System. Vetted over 25 other systems
Randall S. Wood, Associate Corporate Counsel, Cricut
and Gatekeeper rose to the top.
Thank you for requesting your demo.
Next Step - Book a Call
Please book a convenient time for a quick call to discuss your requirements.